Lei Feng network (search "Lei Feng network" public number concerned) : This article Ouyang onions.
Before the formal opening of USB security, it was usual to share an interesting case: At the end of 2014, reports from Reddit that a large company executive computer was infected with a malicious program. The company’s security researchers investigated the source of the malicious program, but checked all traditional possible infections and found nothing. So they began to consider other breakthroughs, starting from the executive's daily diet, turning over and over and checking, and finally found that the problem was actually on the electronic cigarettes of senior executives.
"This is a Chinese-made electronic cigarette. The charging device part contains a hardware-coded malicious program." And this e-cigarette is recharged through the USB port, and this executive will simply insert it into the company for charging. On the computer, the computer is infected with malicious programs.
In this case, if the malicious program is done more secretive, then the entire attack process can even reach the point of no one's consciousness. The core of this is the "USB security" that we want to talk about.

It is inaccurate that we arbitrarily mention the term "USB security." Because USB is essentially just a universal serial bus - there are many buses, SATA bus, PCIe bus, etc. What kind of security topics can this talk about? It may be that USB can be used as a means of spreading malicious programs. We say "USB security" and say "net cable security" is not feeling ridiculous?
However, it is probably because USB is a unified star standard that replaces ancient interfaces. Moreover, USB does not require high licensing fees like interfaces such as Thunderbolt. It is also necessary to use USB interfaces for mass devices in the contemporary world. Interestingly, we often refer to devices that use the USB interface as USB devices (but no one calls the built-in hard disk of the PC as a SATA device or a PCIe device). This is also the basis for talking about USB security here.

Because USB is so widely used today, USB devices have become an important carrier for the spread of malicious programs. However, if we only talk about the USB device as the route of transmission of malicious programs, then any interface actually has the possibility of such transmission. For example, U disk can spread the virus, Thunderbolt mobile hard disk is OK, even the disc can be.
In general, we have to talk about the so-called USB security, not USB security problems in the data transmission process, or a certain type of USB interface specification (such as Type-C) a pin design flaws, but the USB interface or bus As an important way of malicious programs , there are security issues, as well as the security problems of the USB protocol and drivers.
So for USB security, there are 3 points to talk about.
First, USB is a fairly universal standard. Mouse, keyboard, e-cigarette, and external sound card all use a USB interface and are plug-and-play. Therefore, in the physical interface, it is probably the most efficient for the spread of malicious programs except the network adapter interface.
Second, the USB protocol can be exploited by attackers, which will also be the focus of this article.
Third, the most advanced USB 0day vulnerability.

In an age when the Internet is not as popular today, removable storage devices are an important way to spread viruses. Is to put malicious programs on the U disk, or move the hard disk, or even floppy disk - in the process of different PCs to exchange data, it can achieve the role of spread of the virus. The savage malicious program also needs humans to open to run. In operating systems like Windows, to enhance the user experience, the system has an AutoPlay/AutoRun auto-play function for removable storage media.
The original automatic playback function is to insert or play CD/DVD multimedia discs. For Windows installation media, the inserter can immediately eject the installation program. Most of the students should know that the autorun.inf file in the root directory of the removable storage media is responsible for the auto-play function, opening the form as follows:
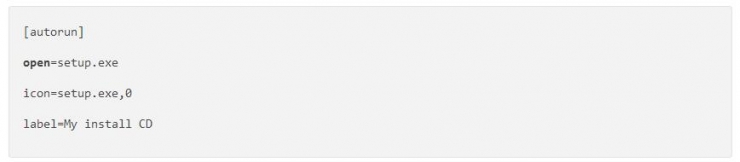
Compared with the optical disk, U disk can be read and write convenience is obviously better, if the setup.exe here is a virus, then the device is inserted into the U disk, the system will automatically run the virus. Therefore, it is very convenient for the virus to use the autorun.inf file to realize the function of inserting a U disk to start a malicious program. Colleagues exchange data, everyone's computers are plugged into a USB flash drive, and they are naturally infected. The infected device is then infected with a new U disk inserted into the device to achieve the purpose of proliferation.
This is a normal way for U-disks to spread malicious programs. As a result, some people refer to autorun.inf as a "U-disk virus," although this is actually innocent. In fact, it is not difficult to put an end to this type of virus transmission. On the one hand, automatic playback or automatic startup of removable storage media is disabled in the system. On the other hand, it is also possible to prohibit programs from creating an autorun.inf file on a USB flash drive. , to achieve U disk will not spread the purpose of the virus.
It can be said that autorun.inf is the most widely spread U disk virus transmission method in the past. Many U disk virus killing tools are mainly for the autorun.inf reclamation. In particular, starting with Windows XP SP2, the system automatically targets the “USB mass storage device†and ZIP drive. Microsoft sees the situation is not good, starting from Windows Vista and Windows Server 2008, for the default behavior of the system to insert a U disk, has been asked to the user whether to perform automatic operation instructions. The era of autorun.inf is almost over.
| Using U disk to fish will not succeed?As mentioned above, in fact, the U disk security issues mentioned above are not exclusive to USB devices. Any mobile storage device (even internal hard disks) has such problems. So strictly speaking, this kind of security problem is simply not surprising on the USB head. If you must blame it, as mentioned above, just because USB is so common.

At the Black Hat USA 2016 hacking conference just concluded recently, Elie Bursztein, head of Google's anti-fraud research team, shared a topic called "Does dropping USB drives really work?" ) He tried to discard 297 U disk around the University of Illinois campus to see if anyone with curiosity would go back and see what was in the U disk. If Bursztein lost 297 SATA3 hard drives (Lol), the attack method is theoretically the same, but how bad the attack effect is can be imagined. It can be seen that the popularity of USB is the basis for our discussion of its security here.
The Computer Industry Association of the United States launched a survey last year that showed that 17% of people will directly connect to a computer after they find the USB device - this data may be too conservative. Bursztein’s findings were significantly more aggressive: 135 U disk (ie 45%) were connected to computers after being taken away. These people also opened the files. The “malicious program†on them returned data to Bursztein. .
Fortunately, this is only an experiment and there is no real "maliciousness". Bursztein's research team did this: They did not use autorun.inf, because the current operating system does not eat this set, and Mac does not support auto-run functionality. Their approach is: Fishing .
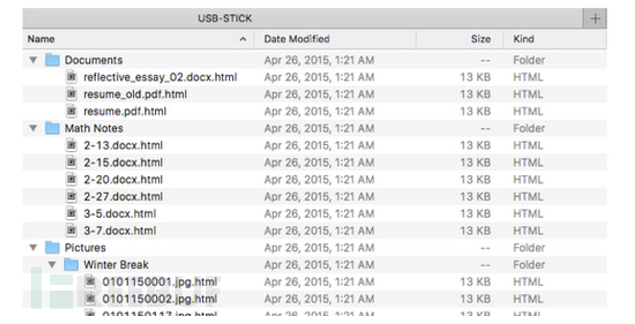
The research team tagged the 297 USB flash drives and even clearly wrote the U disk owner (and return address). Even in this case, 135 USB flash drives were opened by curious students. The files in the USB flash drive confusely written the words "final exam" and "confidential". In fact, these files are all in HTML format. There are pictures in the file and the address of the server of the research team is called. The team knew that someone had opened the file.
In addition, after the HTML document was opened, there was a questionnaire survey asking these curious babies: You guys have to plug in people's U disk! It is true that 20% of people participated in the survey, and over two-thirds said that they actually wanted to return Really?, 18% admitted that they were curious, and 14% gave other explanations.
For this example, we can easily see that the success rate of U disk fishing is still quite high. If these HTML files are replaced with malicious programs, or if the survey questionnaire is changed to a “fishing questionnaire†asking for username and password, how many people will be planted in it? In the American drama "Mr Robot", there appeared a section of a U disk that was used for fishing . It seems that this is not just a legend!

Again, the above two parts actually talked about using the USB device as a carrier to spread malicious programs. It was like U disk fishing, its essence and the loss of a floppy disk to fishing (Lol), and mail fishing is no difference. The original sin is not on the USB device. If you use this method to talk about USB security, there is actually a lot of content to be said, such as USB interface is an important way to invade ATM machines, as well as USB Key as a security means of data decryption, are nothing but to USB as tool.
So is there any original sin of USB? Have! You can start with the USB protocol. USB is not only a MSC (mass storage) device. Now that the USB interface supports such a wide range of functions, the protocol is actually varied. Naturally, there are not only related MSC protocols, but also what USB Power Delivery (USB fast charging specification) and USB OTG (SRP). , HNP protocol, transmission between two peripherals, etc. There is also a USB HID device class protocol. The USB HID here has become the killer of USB device attacks in the past two years.
HID is the Human Interface Device and it is a device that interacts with people. In fact, USB-HID devices are now quite common, such as USB keyboards, mice, and handles. How can this be used? At the Black Hat Hacking Conference in 2014, security researchers Karsten Nohl and Jakob Lell made a speech and mentioned a somewhat shocking USB attack method called BadUSB, which partially exploited the features of HID.

The above is very mysterious, so here's another chestnut: The keyboard is used? Have you ever tried to use the keyboard to perform various system operations without using a mouse? Experienced students should know that it is not difficult. So if there is such a U disk, it can disguise as a keyboard, through the script to perform a series of keyboard stroke operations, is not feeling can control your system? This is actually an example of the Bad USB attack using the USB protocol. The U disk infected by BadUSB not only disguised as a USB keyboard, but also disguised as a USB network card - tampered with the DNS, so that all DNS queries can be sent to the attacker's server and can be redirected .
Once this kind of attack is realized, the attack method will naturally become various, and only one cannot think of it. The most important thing is cross-platform—because the system platforms follow the same USB standard. Details can be found in an article published that year, "Decrypting BadUSB: The Worst USB Devices in the World."
After all, is this HID simulation attack not the USB Rubber Ducky that hackers love so much? The problem is that the internal hardware of the rubber duck is very embarrassing, there is a 60MHz processor, microSD expansion slot. How can ordinary U disk achieve this kind of attack means? This problem is actually the genius of the two researchers Karsten Nohl and Jakob Lell, and it is also the terrible aspect of these U disk after infected with BadUSB.
The composition of general U disk in addition to the flash memory part we need to use to store data, as well as the main control chip, or control chip. The main control chip will usually specify certain parts of the unit for storing the firmware driver (see also the main control chip itself contains the firmware flash memory). The firmware here is similar to an operating system and controls hardware and software interactions. Nohl and Lell spent several months doing reverse engineering. They found that many U-disks can be reprogrammed on the firmware part (especially the PHISON group master chip). The user does not see the firmware part at all, and it is naturally easy to hide the attack code.
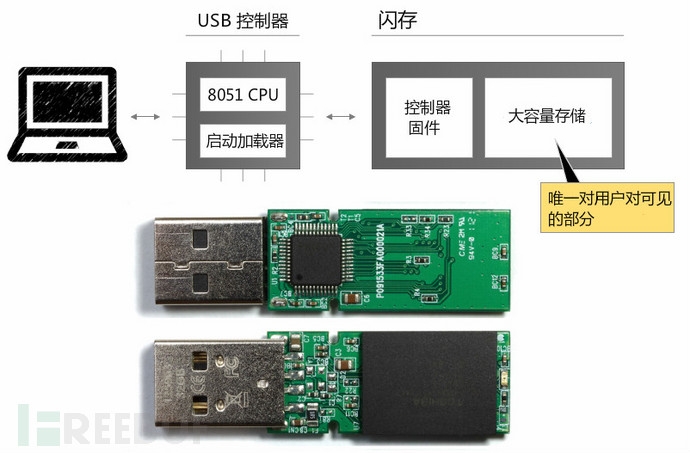
This is where the core of BadUSB is formed. On the other hand, contemporary operating systems provide maximum compatibility with USB devices. The USB standard allows one USB device to have the features of multiple input and output devices. In this way, by rewriting the U disk firmware, it can be disguised as a USB keyboard, network card or even display. Through this fake keyboard, enter the malicious instructions and code in the USB flash drive firmware, and you can also use the malicious program in the flash memory to attack.
To put it plainly, BadUSB is to make ordinary U disk into a rubber duck, and even more aggressive. This enhancement is reflected in the camouflage and spread of BadUSB. camouflage! It is easy to understand, it seems just a normal U disk, and even if you format the U disk can not remove malicious code, because the malicious code in the firmware; spread! When Nohl and Lell specifically mentioned in the research report, the biggest threat to BadUSB's theory is that after a BadUSB device is used to infect a computer with a malicious program, the computer can also spread BadUSB to other U-disks inserted into the computer: A U disk After inserting this computer, the malicious program on the computer can reprogram the U disk firmware, and the U disk owner will not be aware of it.
As a result, U disk around the world can be infected by BadUSB in this way. No U disk in the world can be trusted because no anti-virus software can find it at all. This can even lead to a question: Has the USB device reached the point where there is no security at all?

In fact, it is not entirely, for the U disk firmware, the introduction of unforgeable cryptographic signature mechanism is a kind of program to prevent the rewriting of malicious programs. This mainly depends on the flash memory master chip maker. Because someone accused Nohl that his previous speech on Black Hat was actually only aimed at Taiwan's flash memory master chip - so at the end of 2014, Nohl also sampled the main chip of the 8 major chip manufacturers: Alcor, Renesas, Cheung Shuo (ASUS subsidiary), Genesis, FTDI, Microchip, Cypress.
It was found that the situation was extremely complicated. It is true that some USB master chips are immune to BadUSB—that is, the firmware cannot be reprogrammed. The immunized chips account for half of the total number of samples, but each brand's performance is very unstable. For example, U-disks that use group-based master chips all have the risk of being infected by BadUSB, while Cheung Shuo is completely immune to BadUSB. Genesis USB 2.0 chips are fine, but the updated USB 3.0 chip has problems. The control chips used in other USB Hubs, keyboards, cameras, and mice are even more varied. In fact, even if it is the same model of a USB device manufacturer, they will use different master chips in different batches. For example, there are five to six USB control chips used by Kingston.
After we have to use U disk, we must first open the U disk to see if the model of the master chip does not become?
| As long as the USB interface is not safe!Do not know whether many small partners have not noticed, Snowden exposed NSA's document mentioned an eavesdropping device called Cottonmouth (shown below). This is a USB device that is said to secretly install malicious programs into the target device. Although the document does not elaborate on its specific mechanism, Snowden said: "If this kind of thing that Nohl and Lell discovered has long been used by NSA, I wouldn't be surprised." Perhaps a long time ago, NSA was already This is done, then U disk in our hands...

But this is not all. Since the USB standard allows a USB device to have a variety of input and output device characteristics, then the camouflage of the USB device is actually not limited to only the USB-only BadUSB, and various USB devices may be disguised. From your USB mouse, keyboard, camera, e-cigarette, charging treasure.
In addition to the e-cigarettes mentioned at the beginning of the article, the CCTV exposure at the end of 2014 was “retrofitting and stealing privacyâ€: it seems to be just a charging treasure, but it actually has the ability to store data, especially when the encryption mechanism is not as perfect as it is now. iPhone for data theft. With this in mind, everything around us that seems to use the USB interface seems to have the potential to bring poison and horses. This world is really cruel - maybe you have been locked by the NSA, and your mouse will carry APT Trojans...


At this year's Black Hat USA 2016 conference, Elie Bursztein, who shared the validity of the lost U disk, not only did the experiment of losing the U disk, but also educated people on how to make a complete version of the disguised U disk. From the chip to the final U disk external material molding one-stop, all used are low-cost ready-made materials (click here).
FreeBuf also previously published an article titled "Using Arduino to Quickly Create Tennsy BadUSB". Using the Arduino Leonardo MCU (slightly higher in cost), with the simple code writing of the Arduino IDE, it became a disguised U disk. USB attack device. Whoever wants to be black later, sending him a U disk or charging treasure, is probably more effective than email fishing.
| Ultimate form of USB attackBursztein divided USB attacks into three categories at Black Hat USA 2016: Social Engineering (losing U-disks), HID masquerading, and 0-day exploits. The first two of us have already done a simple analysis in the previous article. The last kind of 0-day exploits were only explained briefly. The main use is the 0-day vulnerability of the USB driver. As long as the computer is plugged into a USB device, Can immediately control the computer.
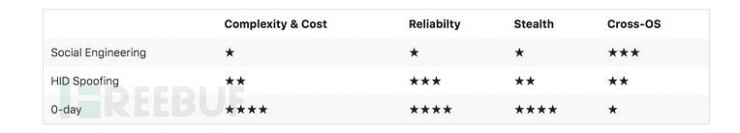
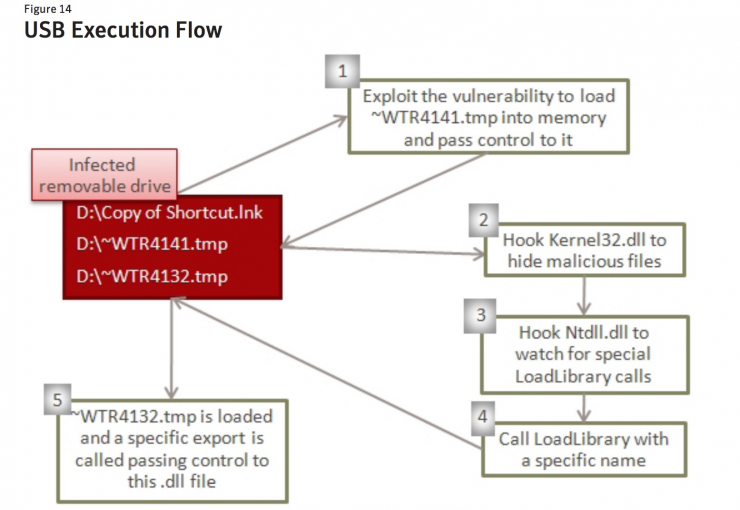
In his view, the 0-day loophole is the level of the USB attack, regardless of the complexity, reliability or concealment has reached the highest level (although because of pertinence, so cross-platform properties are not good). The kind of cases we can list are rare because they have not been widely discussed. The previously famous Stuxnet Stubnet virus used USB (but does not seem to be a 0-day vulnerability in the USB driver). In the Windows system, the .lnk file is responsible for rendering the file icon in the U disk. When inserting the U disk, The resource manager will scan the .lnk files to display the files in various formats. The shock network virus inserts the malicious program into the .lnk file. The entire process is performed by insertion, so its hidden nature can be seen naturally. .
However, such an example is rare, and it takes about a lot of time and effort to conduct targeted attacks. For most people, U disk fishing and HID camouflage are indeed the most need to prevent. But after we talked so much, do we still need to talk about USB security precautions?
Like Nohl, the best solution for preventing USB attacks is not to use USB devices . For this goal, please seal all the USB ports on the device.... Serious, of course, because of bad food is not good, but unidentified U disk or even charging treasure, electronic cigarettes do not use, U disk appears on the road Please also ignore it; your own USB device should not be inserted into untrusted host devices. What users can do is probably only this.
Lei Feng Net Note: This article is FreeBuf special report, the author Ouyang Onion, reproduced, please keep the source and the author, not to delete the content.